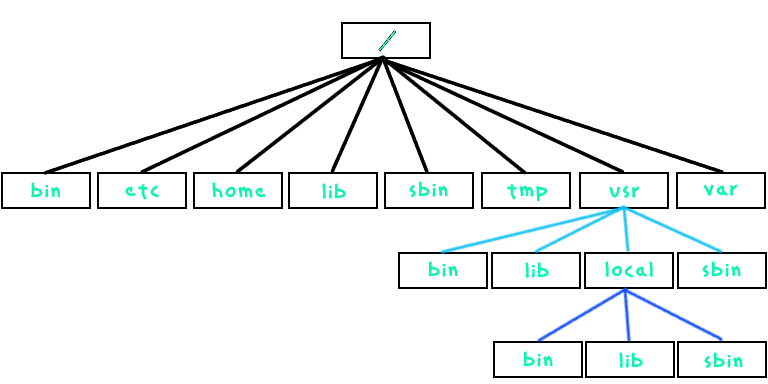
projects
| pct0 (bonus; due 20190822) |
| uxi0 (due 20190822) |
| wcp1 (due 20190822) |
| pct1 (due 20190828) |
| wcp2 (due 20190828) |
| adm0 (due 20190904) |
| pct2 (due 20190904) |
| wcp3 (due 20190904) |
| pbx0 (due 20190911) |
| pct3 (due 20190911) |
| wcp4 (due 20190911) |
| pbx1 (due 20190918) |
| pct4 (due 20190918) |
| wcp5 (due 20190918) |
| pbx2 (due 20190925) |
| pct5 (due 20190925) |
| wcp6 (due 20190925) |
| upf0 (due 20191002) |
| pct6 (due 20191002) |
| wcp7 (due 20191002) |
| upf1 (due 20191009) |
| pct7 (due 20191009) |
| wcp8 (due 20191009) |
| usr0 (due 20191023) |
| pct8 (bonus; due 20191023) |
| pct9 (due 20191023) |
| wcp9 (due 20191023) |
| wpa0 (due 20191030) |
| pctA (due 20191030) |
| wcpA (due 20191030) |
| pwn0 (due 20191106) |
| pctB (due 20191106) |
| wcpB (due 20191106) |
| gfo0 (due 20191113) |
| pctC (due 20191113) |
| wcpC (due 20191113) |
| EoCE (due 20191211 by 172959) |